As part of the Hacking with Hayden series: Metasploit Framework is the most popular and one of the most powerful exploitation frameworks
Featured video: https://www.youtube.com/watch?v=8lR27r8Y_ik&ab_channel=HackerSploit
Metasploit Framework is the most popular and one of the most powerful exploitation frameworks. It is broken into three parts; msfconsole – the main command-line interface, modules – exploits, scanners, payloads, etc, tools – independent tools that help discover vulnerabilities such as msfvenom, pattern_create, and pattern_offset.
Interacting with Metasploit Framework is done by using the ‘msfconsole’ command on a linux machine. This will bring you to the main interface called the console. From here you are able to interact with the different modules within the framework. The msfconsole has many similar commands as the Linux terminal. Metasploit uses tab completion. Meaning if you start typing a command and press the tab key, metasploit will auto complete the command Modules are individual components that each perform a task.
Auxiliary – supporting modules like scanners, fuzzers, and crawlers.
Encoders – allow you to encode the exploit and payload to attempt to mask it from signature-based antivirus protection. Often have a limited success rate as antivirus compare suspicious files to a database of known threats.
Evasion – modules that directly try to evade antivirus software.
Exploits – code that uses a vulnerability on a target system, neatly organized by target system
No Operation (NOPs) – Used as a buffer to achieve consistent payload sizes.
Payloads – code that will run on the target system. There are 3 payload directories: Singles – self-contained payloads that do not need additional components to run. Stagers – Set up a communication channel between Metasploit and the target system. After establishing communication, it will download the rest of the payload (stage). Stages – downloaded by the stagers. Larger downloadable payloads.
Post – Used during post exploitation to maintain some level of access on the target computer and potentially break into the network.
Msfconsole is managed by context. Unless you set a global variable, all settings will return to default if you change modules.
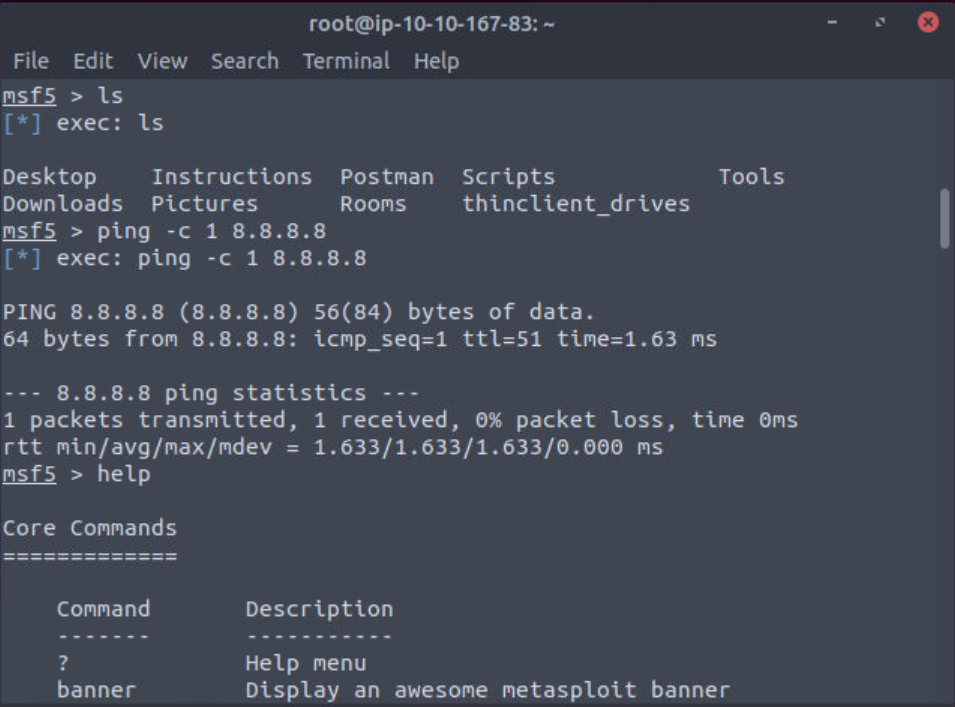
The ‘use’ command followed by the module and module name will change the command prompt from msf6 to the module you have selected. The exploit in the screenshot below is allegedly developed by the NSA and is just used as an example. With the new command prompt, we can still run the previously mentioned commands as we did not enter a folder like with other command lines.
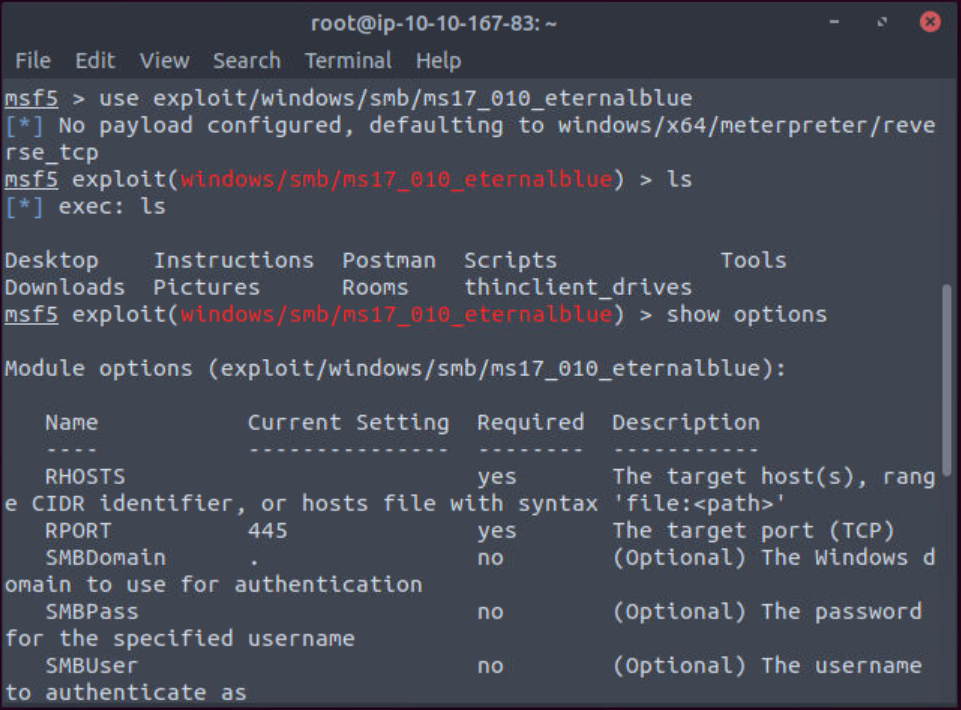
The ‘show’ command followed by a module (payload, exploit, etc) will list available modules. ‘info’ will provide more information on any module.
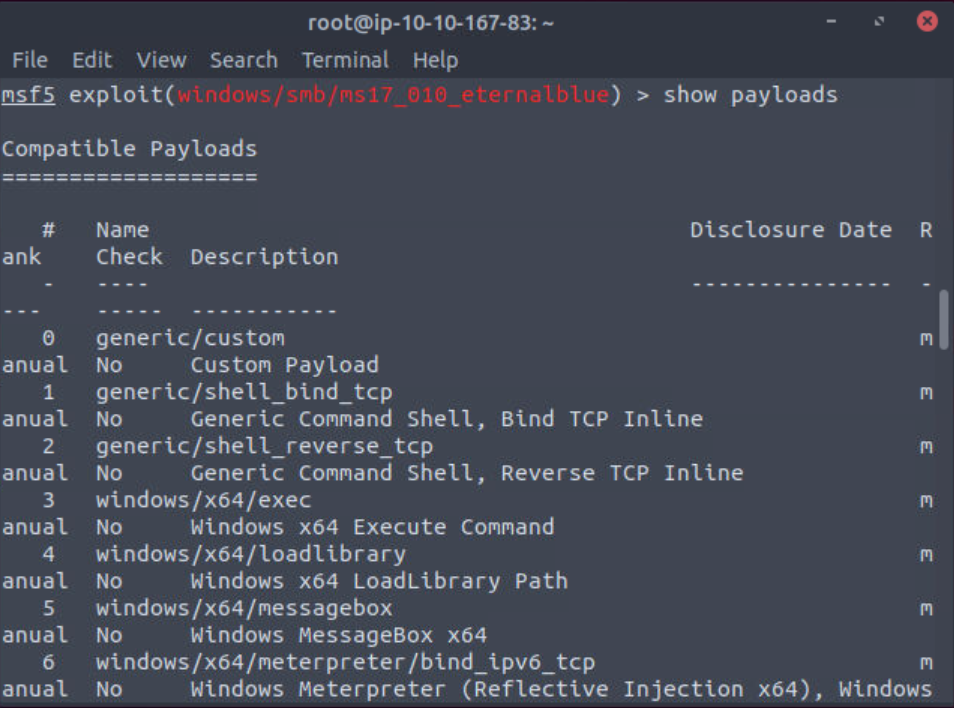
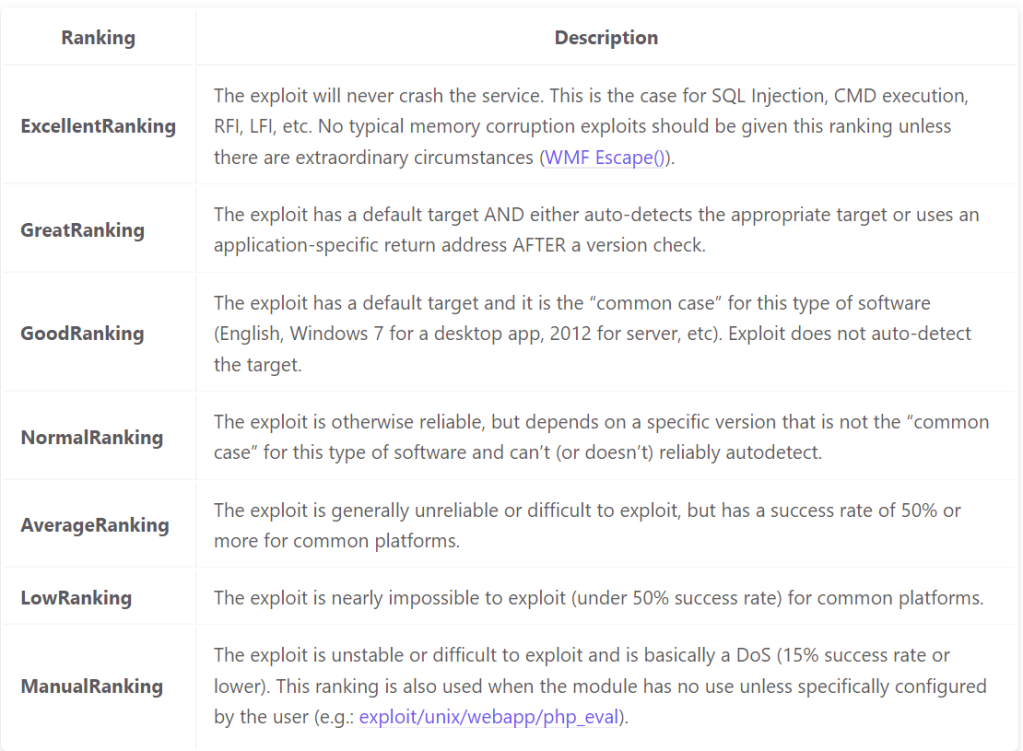
Search – this is the most useful command. Based on the inputted parameters, it will search the Metasploit Framework database. Example searches can include target systems, exploit names, or common vulnerability and exposures (CVE) numbers. An important piece of information given by the search command is the “rank” column. This column ranks exploits by their reliability and is categorized by the screenshot below taken from https://docs.metasploit.com/docs/using-metasploit/intermediate/exploit-ranking.html. These rankings are to be taken with a grain of salt as sometimes low ranking exploits work perfectly and excellent ranked exploits may not work.
For some exploits to work, they require a value for the parameter. Some are pre-populated, but double check to make sure they are the same for your target. Parameters can be overridden by using the set command again with a different value. ‘setg’ sets a global command that will be used by default for all modules. You can clear a global set value with ‘unsetg’ A list of the more popular parameters:
RHOSTS – “Remote host”, the IP address of the target system. You can input a single IP address or a network range. This supports the CIDR notation or network ranges.
RPORT – “remote port”, the port on the target system the vulnerable application is running on.
PAYLOAD – the name of the payload you will use for the exploit.
LHOST – “Localhost”, the attacking machine (your machines) IP address.
SESSION – All connections established with target systems will have a session ID. This will be used for post-exploitation modules.
Once all module parameters are set, you can launch the module using ‘exploit’ or ‘run’. These parameters can be run on their own or with the ‘-z’ parameter. ‘exploit -z’ will run the exploit and background the session when it opens. After a vulnerability has been successfully exploited, a communication channel is established between the target and Metasploit.

Leave a comment